Project description
The objective of DI-P2SL is the implementation of privacy preserving frame manipulation within the transmission chain of openwifi. This manipulation will be designed as a sub-layer of the 802.11 protocol stack. CSI-based localization techniques in 802.11 pose a significant threath to people’s privacy, as they allow tracking the position of a person, at least in an indoor environment, even if she/he does not hold or wear an 802.11 device. This capability is rooted in the information carried by frames from the transmitter to any receiver on the electromagnetic environment, usually called the channel response H(f,t) in classical telecommunication terms. Proper frame initialization allows the extraction of this information from the received frames: the Channel State Information (CSI). The CSI is used to enhance transmission performance, but can also be used to fingerprint the location of a person in a room, as H(f,t) is influenced by the human body, that absorbs, reflects and distorts electromagnetic signals
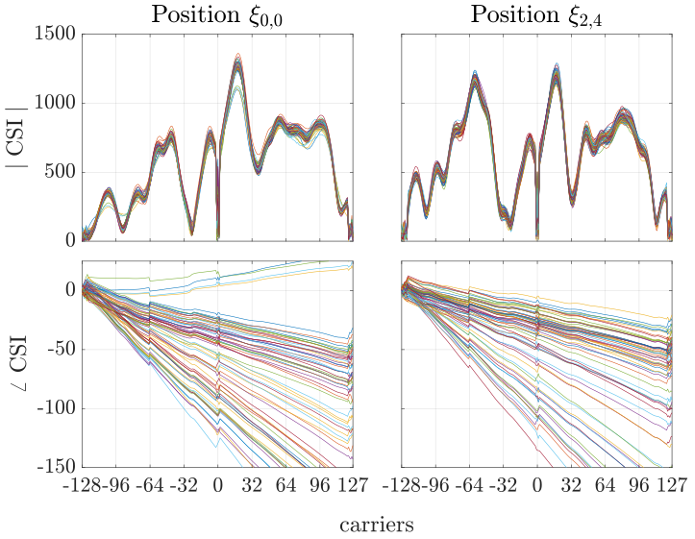
The figure on the left reports the amplitude and phase of H(f,t) (unit of measure are irrelevant for the discussion) collected over several frames when a person was standing in two different positions in our laboratory in Brescia. It is clear that the amplitude differences and the phase jumps are remarkably constant in time (different frames) and specifically located in frequency (i.e., the carriers on the x axis) dependant on the person’s position, hence creating a fingerprint of the location. There is no theoretical framework that allows the derivation of the position of a person directly from H(f,t), but is has been shown several times that Machine Learning (ML) techniques, and Convolutional Neural Networks (CNN) in particular, can be easily trained not only to classify positions based on the fingerprint, but even to infer (x,y) coordinates in a Cartesian space if the training points are sufficiently dense.
The goal of DI-P2SL is the design of a proper obfuscation technique that prevents localization without hampering communications, and its implementation as a sublayer in openwifi.
Obfuscation design
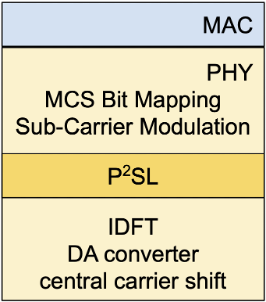
The picture on the left depicts the position of P2SL sublayer on the transmission side within the PHY layer, i.e., between the Sub-Carrier Modulation that builds the OFDM logical symbols and the IDFT that maps them on the digital signal to be converted to the analog signal sent to the antenna after translation in the appropriate 802.11 channel. We note incidentally that OFDM is not a constant envelope modulation, thus the output of the IDFT, in general, does not have a constant amplitude in frequency, hence, even at the local, hardware level, the manipulation done by the M(f,t) distortion may not be so evident and relevant, blending into the normal variation of the signal due to data randomness. In any case P2SL is transparent w.r.t. the data path, so that it can be activated or deactivated during normal configuration of openwifi.
Clearly, the idea is simple, but its design and implementation are far from trivial, and actually involve much more than some modifications in a PHY sublayer. With reference to the openwifi architecture reported on the github project, such a protocol involves modifying the management in User space, the SDR driver in Kernel space and the FPGA, an effort that clearly goes beyond the possibilities of this project.
Potential impact
DI-P2SL is a project with high stakes and ambitious impact at several levels. First of all it helps raise the attention on a privacy issue so far almost completely disregarded: breaches due to hardware leaks rather than data leaks. Second it gives an elegant solution to the problem, since the obfuscation technique we designed, and will implement in openwifi thanks to this project, is a theoretically sound solution that has a strong guarantee to work against any type of attack. Moreover, since all our work results are public and freely available, this ensures that anyone can build on our work without the risk of IPR infringement.
On more prosaic and practical level, DI-P2SL will enhance openwifi significantly, and our connections with Community Networks alternative WISPS, and activists, built thanks to netCommons H2020 project, ensure a high visibility to the project and openwifi. Besides the goal of reducing the digital divide, Community Networks normally do care a lot about privacy and human rights, and they also actively push the adoption of open source projects like openwifi. Some of these communities may serve as early adopters and experimenters, offering openwifi+DI-P2SL “privacy enhanced” APs to their members, even if the hardware cost and maintenance is clearly higher than standard COTS devices.
The DI-P2SL design makes it transparent, i.e., devices implementing it can interoperate with standard 802.11 devices, and as we already explained, it is sufficient that the AP adopts DI-P2SL to properly protect users from passive attacks, i.e., those attacks where the attacker exploits the normal traffic to infer location. This means that privacy aware entities can set up Wi-Fi HotSpots with DI-P2SL-enabled APs, announcing publically the feature, thus further rising awareness on the problem and disseminating our solution. We will actively pursue this line of dissemination, trying to forster experimental adoption, e.g., in Universities or privacy-sensitive environments like Hospitals and Health-Care centers.
It is clear that the largest and deepest impact of DI-P2SL would be the inclusion of the technology into standards or its adoption by some vendors, not necessarily global incumbents, but also SMEs that decide to invest in the (nice?) market of privacy aware people, entities and industries. To pursue this goal, we definitely need to find a funding source.

